
Lucene search
Threat Actors are actively exploiting a SolarWinds Zero-Day Vulnerability
2021-07-1312:50:52
Hive Pro
www.hivepro.com
22
threat actors
exploited vulnerability
solarwinds
serv-u managed file transfer
serv-u secure ftp
patch.
EPSS
0.951
Percentile
99.4%
THREAT LEVEL: Amber.
For a detailed advisory, download the pdf file here.
A zero-day vulnerability (CVE-2021-35211) that impacts the Serv-U Managed File Transfer and Serv-U Secure FTP, is been exploited by multiple threat actors. The PoC of this exploited vulnerability was given to SolarWinds by Microsoft. SolarWinds has released a patch for the same.
Vulnerability Details
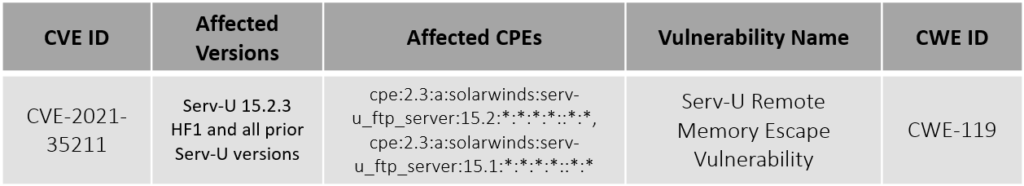
Indicator of Compromise
| Type | Value |
|---|---|
| IP Address | 98.176.196.89 |
| 68.235.178.32 | |
| 208.113.35.58 |
Patch Link
<https://www.solarwinds.com/trust-center/security-advisories/cve-2021-35211>
References
<https://thehackernews.com/2021/07/a-new-critical-solarwinds-zero-day.html>