
Tabnabbing via window.opener [bookwyrm.social]
0.001 Low
EPSS
Percentile
30.3%
Description:
- Hello @bookwyrm-social I found a tabnabbing vulnerability. attack is possible due to
taget=_blankor Tab nabbing via window.opener.
VISIT:- https://bookwyrm.social/
SUMMARY:
- I was browsing the site and found a tabnabbing vulnerability . As per the observation I found that attack is possible due to taget=_blank or Tab nabbing via window.opener. When you open a link in a new tab ( target=“_blank” ), the page that opens in a new tab can access the initial tab and change it’s location using the window.opener property.
STEPS TO REPRODUCE:
-
1- Open the website URL :-
https://bookwyrm.social/ -
2- Right-click and click on inspect element
-
3- Locate the cursor to Element Tab then do
CTRL+F or Search for taget="_blank" -
4- If you get blank with a link it means website can be vulnerable like , open redirect like vulnerabilities
-
5- For More Details To Check the POC
POC Screenshot 1:
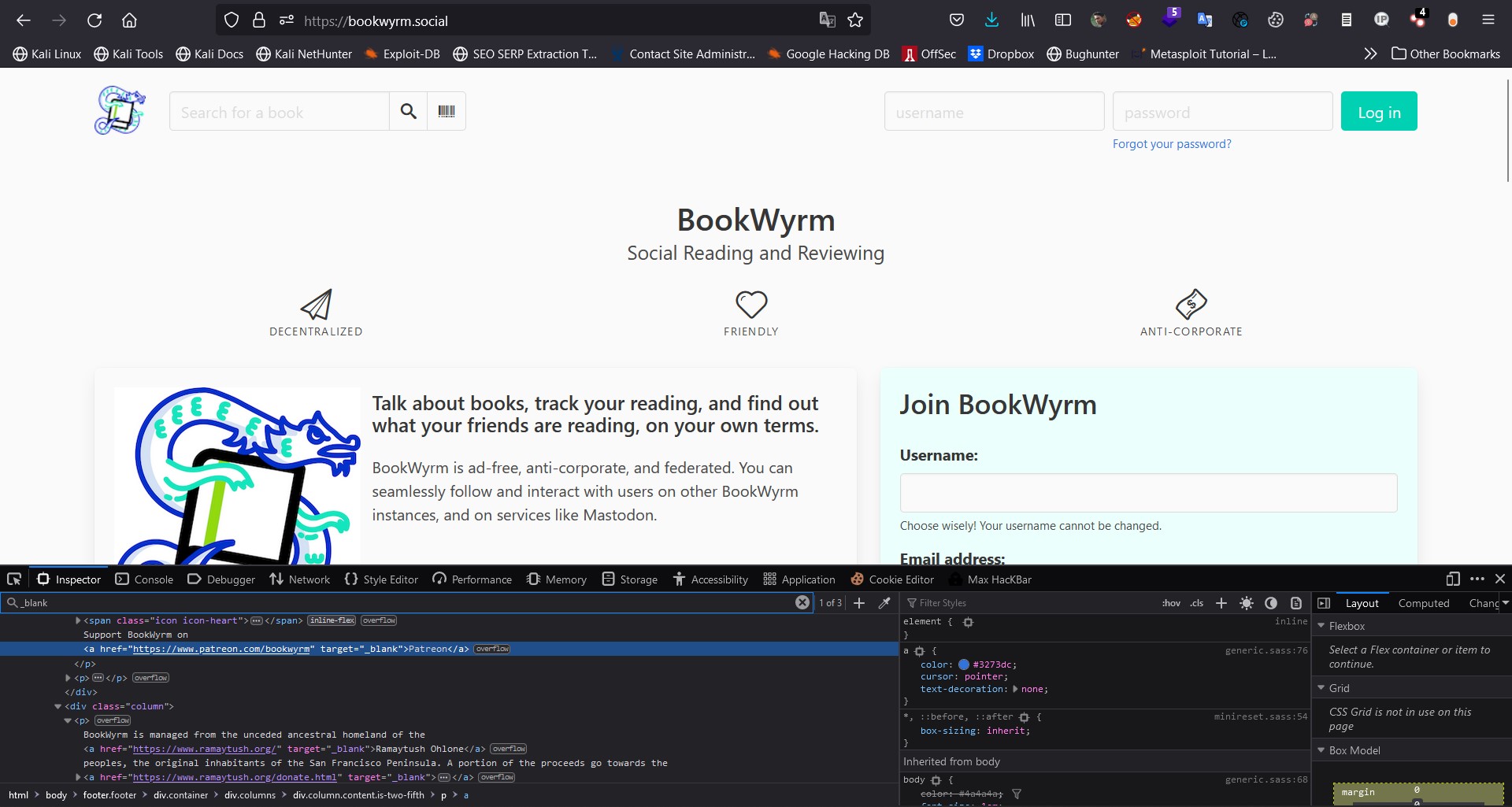
POC Screenshot 2:

MITIGATIONS:-
In order to mitigate this issue, developers are encouraged to use rel=“nofollow noopener noreferrer” as follows:
<a target=“_blank” href=“#"”><i></i>
</a>
Don’t open links in new tabs using the target=“_blank”
Add attribute rel=“noreferrer” which also disables referrer
Set the window.opener attribute to null on the new tab before redirecting, like this: <script>var w=window.open(url, “target=_blank”);w.opener= null;</script>
External links in main domain :
https://www.patreon.com/bookwyrmhttps://www.ramaytush.org/