
Microsoft & Adobe Patch Tuesday (May 2021) – Qualys covers 85 Vulnerabilities, 26 Critical
0.973 High
EPSS
Percentile
99.9%
Microsoft Patch Tuesday – May 2021
Microsoft patched 55 CVEs in their May 2021 Patch Tuesday release, of which 4 are rated as critical severity. Three 0-day vulnerability patches were included in the release. As of this publication date, none have been exploited.
Qualys released 12 QIDs on the same day, providing vulnerability detection and patch management coverage (where applicable) for all 55 CVEs and the related KBs.
Critical Microsoft vulnerabilities patched:
CVE-2021-31181- SharePoint Remote Code Execution Vulnerability
Microsoft released patches addressing a critical RCE vulnerability in SharePoint (CVE-2021-31181). This CVE has a high likelihood of exploitability and is assigned a CVSSv3 base score of 8.8 by the vendor.
CVE-2021-31166- HTTP Protocol Stack Remote Code Execution Vulnerability
Microsoft released patches addressing a critical RCE vulnerability in Windows. This vulnerability allows an unauthenticated attacker to remotely execute code as kernel. This is a wormable vulnerability where an attacker can simply send a malicious crafted packet to the target impacted web-server. CVE has a high likelihood of exploitability and is assigned a CVSSv3 base score of 9.8 by the vendor.
CVE-2021-28476 - Hyper-V Remote Code Execution Vulnerability
Microsoft released patches addressing a critical RCE in Windows Server that impacts Hyper-V. Though the exploitation of this vulnerability is less likely (according to Microsoft), this should be prioritized for patching since adversaries can abuse this vulnerability and cause Denial of Service (DoS) in the form of a bug check. This CVE is assigned a CVSSv3 base score of 9.9 by the vendor.
Three 0-day vulnerabilities patched:
- CVE-2021-31204 - .NET and Visual Studio Elevation of Privilege Vulnerability
- CVE-2021-31207 - Microsoft Exchange Server Security Feature Bypass Vulnerability
- CVE-2021-31200 - Common Utilities Remote Code Execution Vulnerability
Qualys QIDs Providing Coverage
| QID | Title | Severity | CVE ID |
|---|---|---|---|
| 100415 | Microsoft Internet Explorer Security Update for May 2021 | Medium | CVE-2021-26419 |
| 91762 | Microsoft SharePoint Enterprise Server Multiple Vulnerabilities May 2021 | High | CVE-2021-31181 |
| CVE-2021-31173 | |||
| CVE-2021-31172 | |||
| CVE-2021-31171 | |||
| CVE-2021-26418 | |||
| CVE-2021-28478 | |||
| CVE-2021-28474 | |||
| 110381 | Microsoft Office and Microsoft Office Services and Web Apps Security Update May 2021 | High | CVE-2021-31180 |
| CVE-2021-31179 | |||
| CVE-2021-31178 | |||
| CVE-2021-31177 | |||
| CVE-2021-31176 | |||
| CVE-2021-31175 | |||
| CVE-2021-31174 | |||
| CVE-2021-28455 | |||
| 110382 | Microsoft Skype for Business Server Security and Lync Server Update for May 2021 | High | CVE-2021-26421 |
| CVE-2021-26422 | |||
| 375556 | Visual Studio Code Remote Code Execution Vulnerability | High | CVE-2021-31214 |
| CVE-2021-31211 | |||
| 375557 | Visual Studio Code Remote Development for Containers Extension Remote Code Execution Vulnerability | Medium | CVE-2021-31213 |
| 50111 | Microsoft Exchange Server Multiple Vulnerabilities - May 2021 | High | CVE-2021-31209 |
| CVE-2021-31207 | |||
| CVE-2021-31198 | |||
| CVE-2021-31195 | |||
| 91762 | Microsoft Windows Security Update for May 2021 | Critical | CVE-2021-31192 |
| CVE-2021-31188 | |||
| CVE-2021-31170 | |||
| CVE-2021-28476 | |||
| CVE-2021-31184 | |||
| CVE-2021-31190 | |||
| CVE-2021-31167 | |||
| CVE-2021-31168 | |||
| CVE-2021-31208 | |||
| CVE-2021-31169 | |||
| CVE-2021-31165 | |||
| CVE-2021-1720 | |||
| CVE-2021-28479 | |||
| CVE-2021-31185 | |||
| CVE-2021-31194 | |||
| CVE-2021-31191 | |||
| CVE-2021-31186 | |||
| CVE-2021-31205 | |||
| CVE-2021-31193 | |||
| CVE-2021-31187 | |||
| CVE-2020-26144 | |||
| CVE-2020-24587 | |||
| CVE-2020-24588 | |||
| 91763 | Microsoft Visual Studio Security Update for May 2021 | High | CVE-2021-27068 |
| CVE-2021-31204 | |||
| 91764 | Microsoft Windows Web Media Extensions Remote Code Execution Vulnerability | High | CVE-2021-28465 |
| 91766 | Microsoft .NET Core Security Update May 2021 | Medium | CVE-2021-31204 |
| 91767 | Microsoft Windows HTTP Protocol Stack Remote Code Execution Vulnerability - May 2021 | Critical | CVE-2021-31166 |
Adobe Patch Tuesday – May 2021
Adobe addressed 46 CVEs this Patch Tuesday, of which 26 are rated as critical severity, including one critical 0-day (CVE-2021-28550) impacting Adobe Acrobat and Reader product.
Adobe products patches include the following: Experience Manager, InDesign, Illustrator, InCopy, Genuine Service, Acrobat and Reader, Magento, Creative Cloud Desktop Application, Media Encoder, After Effects, Medium, and Animate products.
Qualys released 5 QIDs on the same day, providing vulnerability detection for 30 of the 46 CVEs, including 8 rated as critical.
One 0-day vulnerability patched:
CVE-2021-28550
This is a Remote Code Execution vulnerability impacting Adobe Acrobat and Reader and is being actively exploited in the wild on Windows devices. Adversaries are able to execute arbitrary code in windows, including installing malicious applications and gaining complete access to target machines.
| Adobe Security Bulletin | QID | Severity | CVE ID |
|---|---|---|---|
| APSB21-22 Security updates available for Adobe InDesign | 375549 | Critical | |
| Critical | |||
| Critical | CVE-2021-21098 | ||
| CVE-2021-21099 | |||
| CVE-2021-21043 | |||
| APSB21-24 Security update available for Adobe Illustrator | 375551 | Critical | |
| Critical | |||
| Critical | |||
| Critical | |||
| Critical | CVE-2021-21101 | ||
| CVE-2021-21103 | |||
| CVE-2021-21104 | |||
| CVE-2021-21105 | |||
| CVE-2021-21102 | |||
| APSB21-29 Security update available for Adobe Acrobat and Reader | 375547 | Important | |
| Critical | |||
| Important | |||
| Critical | |||
| Important | |||
| Critical | |||
| Critical | |||
| Critical | |||
| Critical | |||
| Critical | |||
| Important | |||
| Critical | |||
| Critical | |||
| Critical | CVE-2021-28561 | ||
| CVE-2021-28560 | |||
| CVE-2021-28558 | |||
| CVE-2021-28557 | |||
| CVE-2021-28555 | |||
| CVE-2021-28565 | |||
| CVE-2021-28564 | |||
| CVE-2021-21044 | |||
| CVE-2021-21038 | |||
| CVE-2021-21086 | |||
| CVE-2021-28559 | |||
| CVE-2021-28562 | |||
| CVE-2021-28550 | |||
| CVE-2021-28553 | |||
| APSB21-32 Security update available for Adobe Media Encoder | 375550 | Important | CVE-2021-28569 |
| APSB21-35 Security update available for Adobe Animate7 | 375553 | Important | |
| Important | |||
| Important | |||
| Important | |||
| Important | |||
| Critical | |||
| Critical | CVE-2021-28572 | ||
| CVE-2021-28573 | |||
| CVE-2021-28574 | |||
| CVE-2021-28575 | |||
| CVE-2021-28576 | |||
| CVE-2021-28578 | |||
| CVE-2021-28577 |
Discover Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:50111 OR qid:91762 OR qid:91763 OR qid:91764 OR qid:91766 OR qid:91767 OR qid:100415 OR qid:110380 OR qid:110381 OR qid:110382 OR qid:375547 OR qid:375549 OR qid:375550 OR qid:375551 OR qid:375553 OR qid:375556 OR qid:375557)
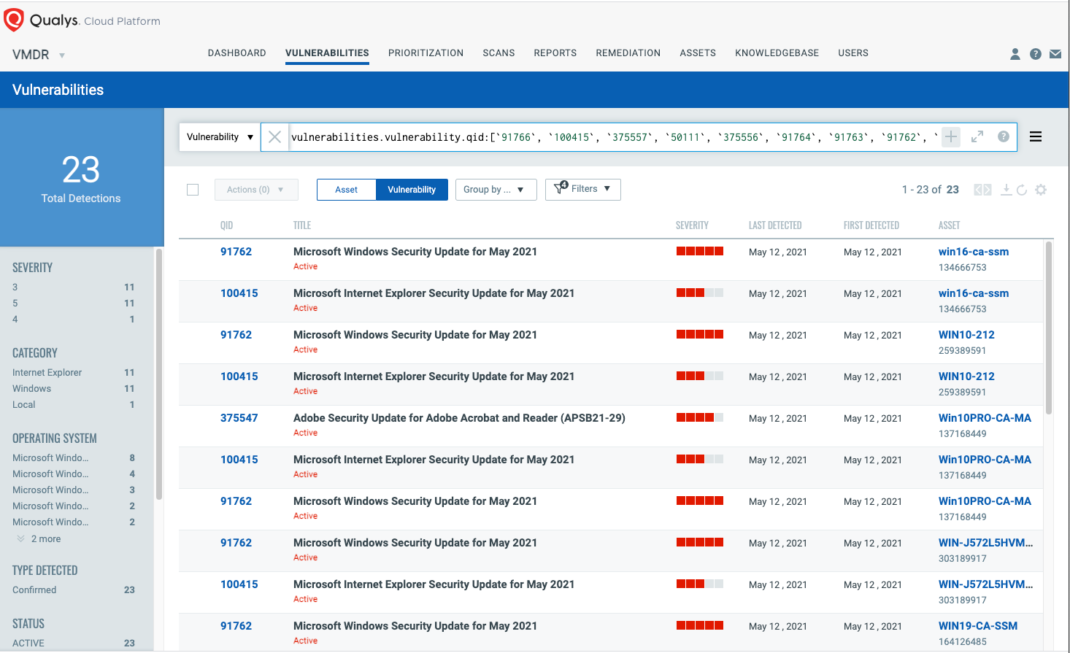
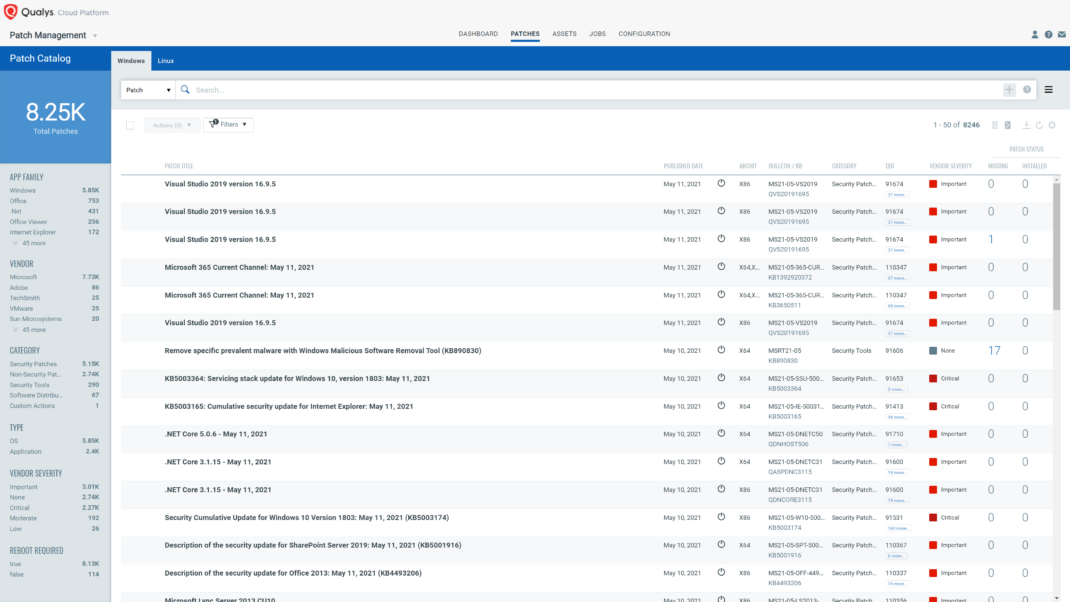
Respond by Patching
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday.
qid:50111 OR qid:91762 OR qid:91763 OR qid:91764 OR qid:91766 OR qid:91767 OR qid:100415 OR qid:110380 OR qid:110381 OR qid:110382 OR qid:375547 OR qid:375549 OR qid:375550 OR qid:375551 OR qid:375553 OR qid:375556 OR qid:375557``
Patch Tuesday Dashboard
The current updated Patch Tuesday dashboards are available in Dashboard Toolbox: 2021 Patch Tuesday Dashboard.
Webinar Series: This Month in Patches
To help customers leverage the seamless integration between Qualys VMDR and Patch Management and reduce the median time to remediate critical vulnerabilities, the Qualys Research team is hosting a monthly webinar series This Month in Patches.
We discuss some of the key vulnerabilities disclosed in the past month and how to patch them:
- 21Nails Exim Mail Server Multiple Vulnerabilities
- Pulse Connect Secure Remote Code Execution Vulnerability (CVE-2021-22893)
- Microsoft Patch Tuesday, May 2021
Join us live or watch on demand!
About Patch Tuesday
Patch Tuesday QIDs are published at Security Alerts, typically late in the evening of Patch Tuesday, followed shortly after by PT dashboards.