
Critical Cisco 0day Exploited – Do you have Blind Spots in your Risk Management?
0.853 High
EPSS
Percentile
98.6%
In the dynamic realm of cybersecurity, the importance of exhaustive vulnerability management and robust risk assessment is paramount. While agent-based solutions have garnered favor among organizations bolstering their cyber protections, it prompts the question: "Is an agent-only strategy truly enough?" While agents provide invaluable insights, a well-rounded understanding and comprehensive risk assessment may require a broader perspective. Data from the National Vulnerability Database (NVD) shows that 82% of high-risk vulnerabilities are associated with a network access vector, underscoring that the vast majority can be exploited remotely.
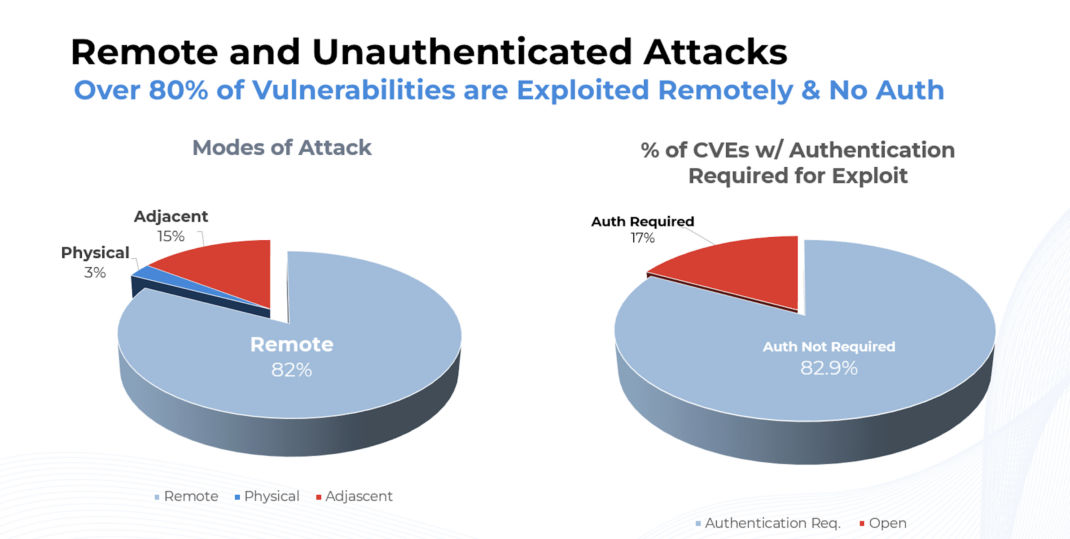 Fig 1: Attack Vector Analysis Revealing Network Dominance in High-Risk Vulnerabilities
Fig 1: Attack Vector Analysis Revealing Network Dominance in High-Risk Vulnerabilities
The recent disclosure of an unpatched critical zero-day vulnerability (CVE-2023-20198) in Cisco's IOS XE software highlights the vulnerabilities inherent in modern IT infrastructure. Currently, under active exploit and added to CISA KEV, this flaw allows unauthorized attackers remote, full-privilege access to affected devices, rendering them entirely under the attacker's control.
This incident highlights a critical point: while agent-based vulnerability management tools are instrumental in monitoring and detecting potential threats on devices they're installed on, they aren't a cure-all. Consider network devices, like the affected Cisco gear. These devices often don't support agents and thus could be blind spots in an agent-only vulnerability management strategy.
Further, the speed at which such zero-day vulnerabilities can be exploited emphasizes the need for a multi-faceted approach to vulnerability management. While agents can provide near real-time alerts, there are situations, such as the present Cisco case, where immediate external interventions, like turning off a feature are needed even before an official patch is released.
Relying solely on agent-based solutions might not grant a complete risk assessment, underscoring the need for a multifaceted approach, among the pivotal reasons are:
- Endpoint Restrictions: Not all endpoints support or have agents installed, leading to potential assessment gaps. Moreover, not all devices in your environment can or should have an agent installed. Infrequently connected devices like off-site servers may also evade regular scans. You need to scan these devices externally to avoid vulnerabilities.
- Infrastructure Complexity: Many network devices, like routers, switches, firewalls, IoT, and OT devices, don't support agents, posing potential risk assessment blind spots.
- Cloud & Virtual Environments: Agent-only solutions might only provide a partial view of cloud-based infrastructure, especially when dealing with containers, serverless functions, and other dynamic cloud-native constructs.
- Configuration Checks: Agent-based solutions are excellent for vulnerability checks but may be less effective in assessing misconfigurations, which can be as risky as known vulnerabilities.
- External Exposures: Agents are great for assessing the state of a device from its perspective. However, they might not capture how the device looks from an external perspective, i.e., how it might appear to an external attacker. Periodic external scans are essential to fill this gap.
- Ensuring Redundancy for Robust Defense: Consider Qualys' approach a multi-layered shield. While one wouldn't solely rely on a single layer of security in modern network architectures, vulnerability management benefits from a diverse strategy. Qualys harmoniously merges agent data with network scans, creating a redundant system. This ensures that potential vulnerabilities are detected and addressed, no matter how hidden.
How Does the Qualys Platform Elevate Your Cybersecurity?
In the face of evolving cyber threats, tools like the Qualys platform stand out for their comprehensive coverage. With holistic asset management, Qualys offers an unmatched lens into an organization's IT ecosystem, covering on-premises, cloud, mobile, OT, and IoT assets. Real-time alerts on vulnerabilities and misconfigurations allow entities to be proactive. Moreover, by harnessing advanced threat intelligence and machine learning, Qualys narrows the focus on pivotal vulnerabilities, ensuring efficient responses.
The true strength of the Qualys platform lies in its unified security and compliance approach. It's not just about detection; it's about effective action. The platform can auto-deploy patches, isolate suspicious devices, and present a consolidated dashboard view for a clear picture of the threat landscape. Whether it's infrastructure security, web app defenses, DevOps integration, or endpoint protection, Qualys streamlines these tasks. Its scalability, precision, and comprehensive coverage cement its role as an indispensable tool for modern organizations.
In light of the CVE-2023-20198 incident, it's evident that organizations face significant and evolving cyber risks that must be managed differently. Sole dependence on agent-based solutions can overlook vulnerabilities in crucial devices and systems, and many cybersecurity strategies lack vulnerability prioritization methodologies that can scale across an organizations’ IT an SecOps stack. Adopting a well-rounded vulnerability management strategy that integrates agent-based and agent-less methods is essential; by harnessing the strengths of diverse approaches, organizations can pinpoint vulnerabilities and take robust measures to curb potential threats.
Qualys not only supports agents but also does network scans, external scans, and passive scans to provide organizations with a comprehensive view. The Qualys platform elevates your cybersecurity by offering a comprehensive and proactive approach that empowers businesses to stay ahead in the cybersecurity game.