Apache Shiro remote security restriction bypass Vulnerability, CVE-2016-6802)
0.003 Low
EPSS
Percentile
69.5%
> Apache Shiro before 1.3.2 allows attackers to bypass intended servlet filters and gain access by leveraging the use of a non-root servlet context path.
shiro in the path control, the attacker can bypass the filter to access filtered path, the impact of the version shrio <1.3.2
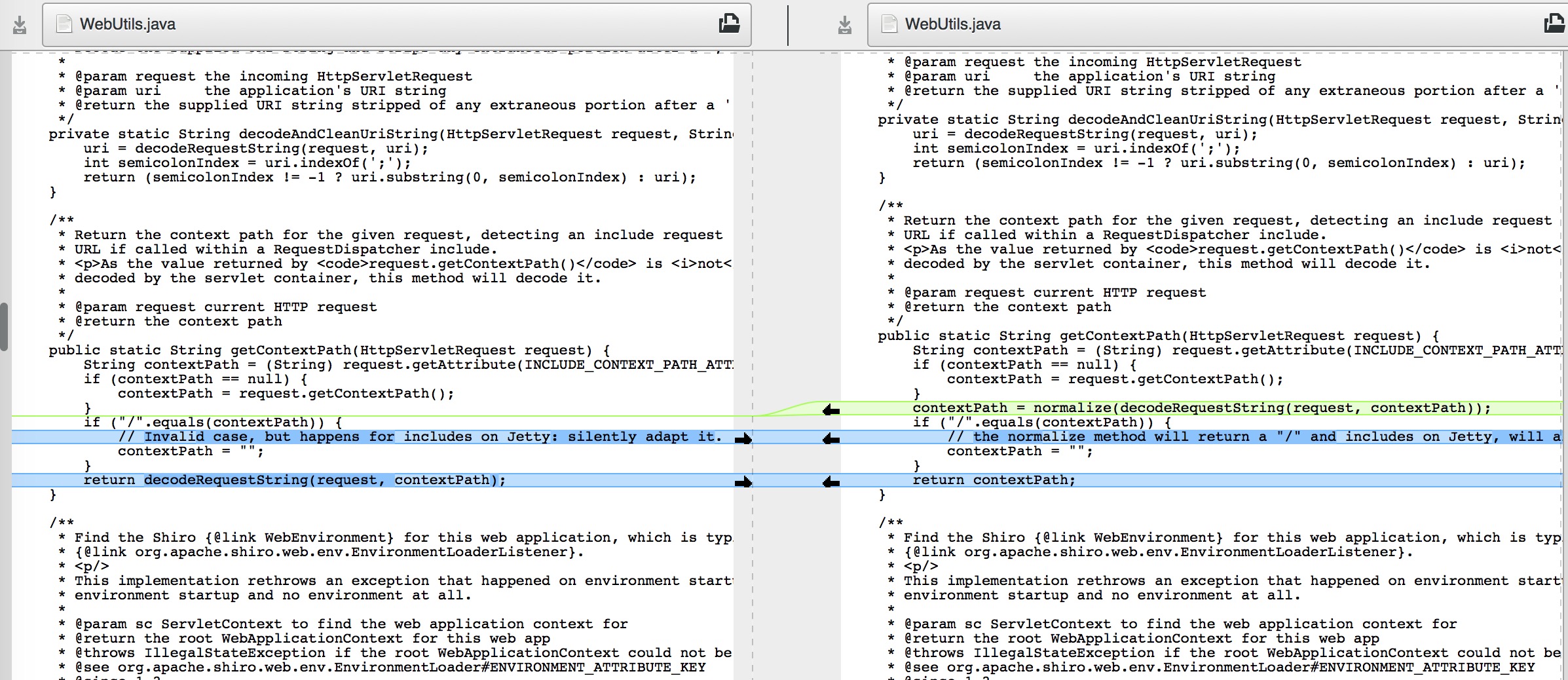
From the above figure it is clear to the latest version of the modified code, as follows
Official repair process
The latest 1. 3. 2 version for the request url processing to add the contextPath = normalize(decodeRequestString(request, contextPath)); i.e., the first of the url to decode, then back to normal, next enter the treatment process.
POC
For example, an ordinary user access the admin account path will appear when 403, this time using the burp cut off, then the access path of the added last%2f, both can be bypassed shiro detection. Because for the browser to say that%2f will be automatically encoded as/, but the burp truncated after entering the shiro, the shiro does not decode it, so it can be bypassed.