New 'CacheOut' Attack Leaks Data from Intel CPUs, VMs and SGX Enclave
0.0005 Low
EPSS
Percentile
18.2%
Another month, another speculative execution vulnerability found in Intel processors.
If your computer is running any modern Intel CPU built before October 2018, it’s likely vulnerable to a newly discovered hardware issue that could allow attackers to leak sensitive data from the OS kernel, co-resident virtual machines, and even from Intel’s secured SGX enclave.
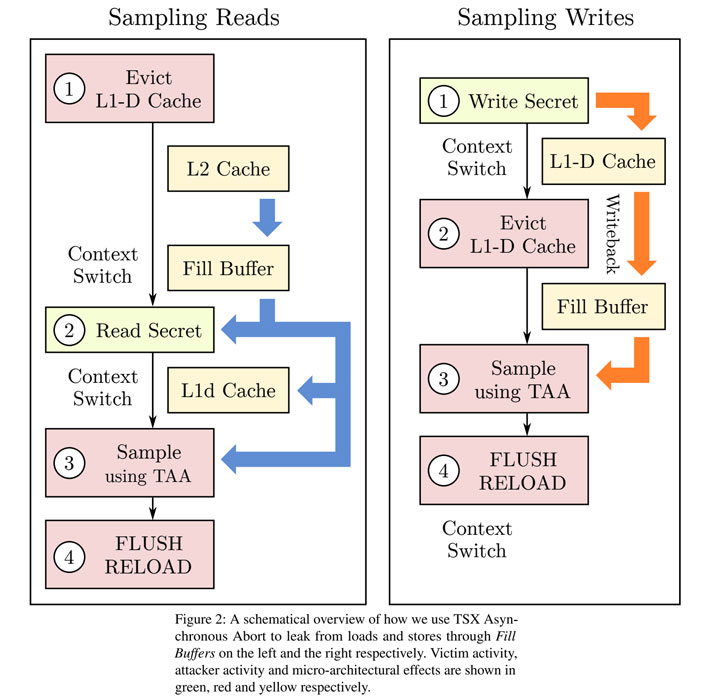
Dubbed CacheOut a.k.a. L1 Data Eviction Sampling (L1DES) and assignedCVE-2020-0549, the new microarchitectural attack allows an attacker to choose which data to leak from the CPU’s L1 Cache, unlike previously demonstrated MDS attacks where attackers need to wait for the targeted data to be available.
According to a team of academic researchers, the newly-discovered speculative execution attacks can leak information across multiple security boundaries, including those between hyper-threads, virtual machines, and processes, and between user space and the operating system kernel, and from SGX enclaves.
“CacheOut can leak information from other processes running on the same thread, or across threads on the same CPU core,” the researchers said. “CacheOut violates the operating system’s privacy by extracting information from it that facilitates other attacks, such as buffer overflow attacks.”
More precisely, the attack enables a malicious program to force the victim’s data out of the L1-D Cache into leaky buffers after the operating system clears them, and then subsequently leak the contents of the buffers and obtain the victim’s data.
Researchers at the universities of Adelaide and Michigan demonstrated:
- the effectiveness of CacheOut in violating process isolation by recovering AES keys and plaintexts from an OpenSSL-based victim,
- practical exploits for completely de-randomizing Linux’s kernel ASLR, and for recovering secret stack canaries from the Linux kernel,
- how CacheOut effectively violates the isolation between two virtual machines running on the same physical core,
- how CacheOut could also be used to breach the confidentiality SGX guarantees by reading out the contents of a secure enclave,
- how some of the latest Meltdown-resistant Intel CPUs are still vulnerable, despite all of the most recent patches and mitigations.
Besides this, according to researchers, it’s currently unlikely for Antivirus products to detect and block CacheOut attacks, and since the exploit does not leave any traces in the traditional log file, it’s also “very unlikely” to identify whether someone has exploited the flaw or not.
To be noted, CacheOut flaw can’t be exploited remotely from a web browser and also doesn’t affect AMD processors.
Based on researchers findings, Intel yesterday released new microcode updates for affected processors that eventually turns off Transactional Memory Extension (TSX) on the CPUs.
“Software [update] can mitigate these issues at the cost of features and/or performance. We hope that somewhere in the future, Intel will release processors with in-silicon fixes against this issue,” the researchers said.
Though most cloud providers have rolled out patches to their infrastructures, other users can also mitigate the cross-thread leakage by disabling Intel hyper-threading for systems where security is more important.
Furthermore, neither Intel nor the researchers have released exploit code, which indicates there’s no direct and immediate threat.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.