New RIG Exploit Kit Campaign Infecting Victims' PCs with RedLine Stealer
0.041 Low
EPSS
Percentile
92.2%
A new campaign leveraging an exploit kit has been observed abusing an Internet Explorer flaw patched by Microsoft last year to deliver the RedLine Stealer trojan.
“When executed, RedLine Stealer performs recon against the target system (including username, hardware, browsers installed, anti-virus software) and then exfiltrates data (including passwords, saved credit cards, crypto wallets, VPN logins) to a remote command and control server,” Bitdefender said in a new report shared with The Hacker News.
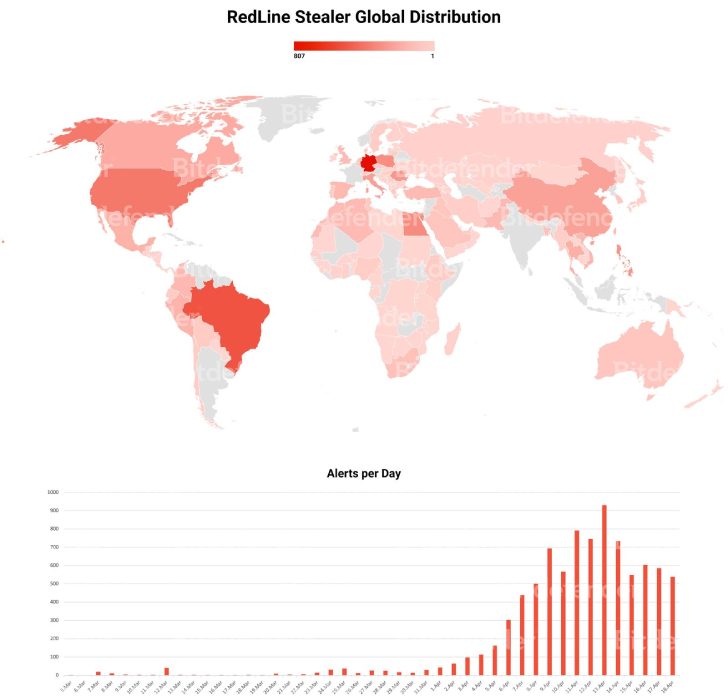
Most of the infections are located in Brazil and Germany, followed by the U.S., Egypt, Canada, China, and Poland, among others.
Exploit kits or exploit packs are comprehensive tools that contain a collection of exploits designed to take advantage of vulnerabilities in commonly-used software by scanning infected systems for different kinds of flaws and deploying additional malware.
The primary infection method used by attackers to distribute exploit kits, in this case the Rig Exploit Kit, is through compromised websites that, when visited, drops the exploit code to ultimately send the RedLine Stealer payload to carry out follow-on attacks.
The flaw in question is CVE-2021-26411 (CVSS score: 8.8), a memory corruption vulnerability impacting Internet Explorer that has been previously weaponized by North Korea-linked threat actors. It was addressed by Microsoft as part of its Patch Tuesday updates for March 2021.
“The RedLine Stealer sample delivered by RIG EK comes packed in multiple encryption layers […] to avoid detection,” the Romanian cybersecurity firm noted, with the unpacking of the malware progressing through as many as six stages.
RedLine Stealer, an information-stealing malware sold on underground forums, comes with features to exfiltrate passwords, cookies and credit card data saved in browsers, as well as crypto wallets, chat logs, VPN login credentials and text from files as per commands received from a remote server.
This is far from the only campaign that involves the distribution of RedLine Stealer. In February 2022, HP detailed a social engineering attack using fake Windows 11 upgrade installers to trick Windows 10 users into downloading and executing the malware.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.