Experts Uncover Spyware Attacks Against Catalan Politicians and Activists
0.028 Low
EPSS
Percentile
90.7%
A previously unknown zero-click exploit in Apple’s iMessage was used to install mercenary spyware from NSO Group and Candiru against at least 65 individuals as part of a “multi-year clandestine operation.”
“Victims included Members of the European Parliament, Catalan Presidents, legislators, jurists, and members of civil society organizations,” the University of Toronto’s Citizen Lab said in a new report. “Family members were also infected in some cases.”
Of the 65 individuals, 63 were targeted with Pegasus and four others were infected with Candiru, with iPhones belonging to at least two compromised with both. The incidents are said to have mostly occurred between 2017 and 2020.
The attacks involved the weaponization of an iOS exploit dubbed HOMAGE that made it possible to penetrate the devices running versions prior to iOS 13.2, which was released on October 28, 2019. It’s worth noting that the latest version of iOS is iOS 15.4.1.
Although the intrusions have not been attributed to a specific government or entity, the Citizen Lab implied a connection to the Spanish authorities based on a “range of circumstantial evidence,” citing ongoing tensions between the country and the autonomous community of Catalonia amid calls for Catalan’s independence.
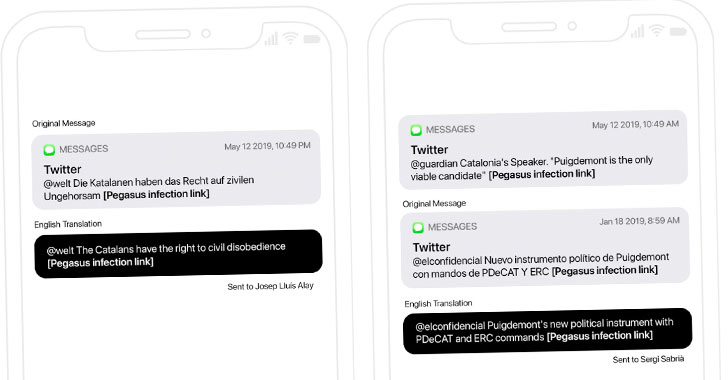
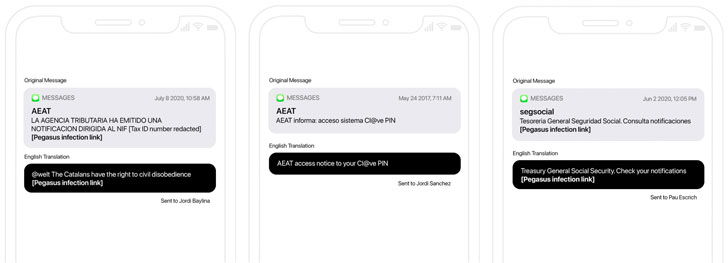
The findings build on a prior report from The Guardian and El País in July 2020 that revealed a case of domestic political espionage aimed at Catalan pro-independence supporters using a vulnerability in WhatsApp to deliver the Pegasus surveillanceware.
Besides relying on the now-patched WhatsApp vulnerability (CVE-2019-3568), the attacks made use of multiple zero-click iMessage exploits and malicious SMS messages to hack Catalan targets’ iPhones with Pegasus over a three year period.
“The HOMAGE exploit appears to have been in use during the last months of 2019, and involved an iMessage zero-click component that launched a WebKit instance in the com.apple.mediastream.mstreamd process, following a com.apple.private.alloy.photostream lookup for a Pegasus email address,” the researchers said.
The issue is likely believed to have been closed by Apple in version iOS 13.2, as the exploit was observed as being fired only against devices running iOS versions 13.1.3 and lower. Also put to use is another exploit chain called KISMET that was present in iOS 13.5.1.
On the other hand, the four individuals who were compromised with Candiru’s spyware were victims of an email-based social engineering attack designed to trick the victims into opening seemingly legitimate links about COVID-19 and messages impersonating the Mobile World Congress (MWC), an annual trade show that takes place in Barcelona.
Both Pegasus and Candiru’s spyware (called DevilsTongue by Microsoft) are engineered to covertly gain extensive access to sensitive information stored in mobile and desktop devices.
“The spyware […] is capable of reading texts, listening to calls, collecting passwords, tracking locations, accessing the target device’s microphone and camera, and harvesting information from apps,” the researchers said. “Encrypted calls and chats can also be monitored. The technology can even maintain access to victims’ cloud accounts after the infection has ended.”
The links to NSO Group’s Pegasus and Candiru stem from infrastructure overlaps, with the hacking operations likely the work of a customer with ties to the Spanish government owing to the timing of the attacks and the victimology patterns, the Citizen Lab said.
“The case is notable because of the unrestrained nature of the hacking activities,” the researchers concluded.
“If the Spanish government is responsible for this case, it raises urgent questions about whether there is proper oversight over the country’s intelligence and security agencies, as well as whether there is a robust legal framework that authorities are required to follow in undertaking any hacking activities.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.