
Intel Memory Bug Poses Risk for Hundreds of Products
CVSS2
Attack Vector
LOCAL
Attack Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:N/I:N/A:C
CVSS3
Attack Vector
PHYSICAL
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
AI Score
Confidence
High
EPSS
Percentile
29.7%
Chipmaker Intel is reporting a memory bug impacting microprocessor firmware used in “hundreds” of products. According to an advisory issued by the company on Tuesday, the bug is firmware-based and rated as “high” risk with a Common Vulnerability Scoring System (CVSS) score of 7.
The vulnerability resides inside some of the Intel Optane SSD and Intel Optane Data Center (DC) products, the impact of which allows privilege escalation, denial of service (DoS), or information disclosure.
Intel has released the firmware updates and prescriptive guidance for Optane SSD Bugs that first surfaced a year ago.
Solid-state drives (SSD) are used for data storage. Intel optane memory is a system acceleration solution that is used to increase the response time to end-user requests, the Optane memory is installed between the processor and slower storage devices (SATA HDD, SSHD, SSD). The optane memory stores commonly used data and programs closer to the processor.
The Intel Optane Data Center SSD is used to eliminate data center storage bottlenecks and provides storage for bigger and more affordable data sets, thus optimizing the overall performance.
Vulnerability Details
According to Intel, it has the CVSS base score of 7.9 and is described as a Race condition within a thread in Intel Optane SSD and Intel Optane SSD DC products. An attacker gaining privileged user access may perform a denial-of-service attack via local access.
The race condition occurs when two thread tries to access a shared variable at the same time.
This vulnerability is described as insufficient control flow management in firmware for Intel SSD and Intel SSD DC products. An unauthenticated user might leverage this vulnerability to perform privilege escalation via physical access.
It has a CVSS base score of 7.3
An attacker can perform information disclosure or privilege escalation via physical access on Intel SSD DC, Intel Optane SSD, and Intel Optane SSD DC products. The vulnerability is caused because of the exposure of sensitive information due to unclear debug information in firmware.
It has a CVSS base score of 7.3
Intel also revealed five additional vulnerabilities which are rated as medium. List of which is given below:
Affected Products
Intel has released a list of its products that are affected by these vulnerabilities.
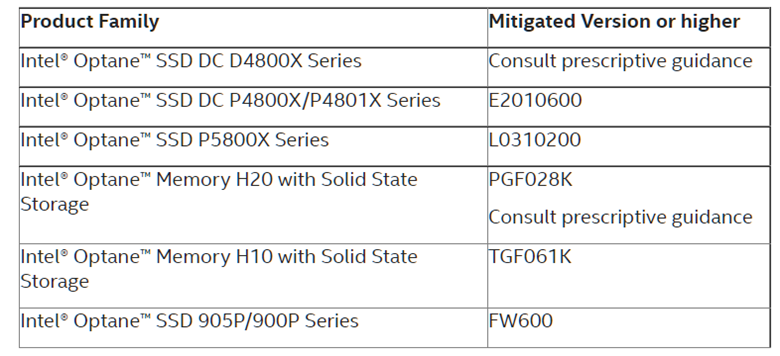
The affected products include all versions of Intel Optane SSD DC D4800X and P4800X/P4801X Series including the previous version E2010600. The Intel Optane SSD P5800X Series before version L3010200 as well as 905P/900P Series all versions are affected.
The affected products also include Intel optane memory H10 and H20 with Solid State Storage Series for all versions.
The customer with affected Intel SSD or Intel SSD DC NAND products should consult the security advisory or contact Solidigm.
Recommendations and Updates
Updates were released by Intel and can be downloaded here, the advisory issued by Intel also includes a possible workaround for CVE-2021-33082.
References
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33069
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33074
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33075
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33077
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33078
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33080
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33082
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33083
[email protected]
www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00563.html
www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00563.html
www.intel.com/content/www/us/en/support/products/35125/memory-and-storage.html#support-product-selector
www.solidigmtechnology.com/en/support.html
CVSS2
Attack Vector
LOCAL
Attack Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:N/I:N/A:C
CVSS3
Attack Vector
PHYSICAL
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
AI Score
Confidence
High
EPSS
Percentile
29.7%